Is your PC not running as smoothly as it did when you first took it out of the box? A lethargic machine is oftentimes the result of a fragmented hard drive, an overabundance of junk files, and a Windows registry in disarray. If youd like to put some pep in the step of your sluggish desktop or laptop, then check out TuneUp Utilities 2013.
This application is designed to improve computer performance by tossing junk files, uninstalling unneeded programs, defragmenting the hard drive, and much, much more.
Overall, the software does a fine job of revitalizing a worn PC, but the license limitations keep it from reaching the heights of the Editors Choice award-winning.Getting Started
Compatible with Windows 8, 7, Vista, and XP PCs, TuneUp Utilities 2013 requires just an Internet connection for activating the license and receiving updates. Unlike Iolo System Mechanics 11, the Editors Choice among paid tuneup utilities, TuneUp Utilities 2012 limits you to only three installs.
When you first fire up the program, youre prompted to run a system scan that will dig up registry and defragmentation problems, as well as other issues. Afterward, you can either run the one-click cleanup or go to the Start Center to check out all the features. I went with the latter option.

TuneUp Utilities installation is relatively painless while taking up no more than 80MB of disk space. The program does require you to consent to sharing information about your machine in order to install. This is so TU can send system information to their server and check if there are any recent updates to the software or OS of your computer. Upon installation, 1-Click Maintenance will ask to run. This is the core of the utility. 1-Click will check everything including the registry, registry fragmentation, application shortcuts, Windows and program files, and hard disk fragmentation to find things that could use tidying up. These are some pretty standard protocols. Regular users will be satisfied with the 1-Click Maintenance tool as it is the main tool of TuneUp. After a successful scan, 1-Click will list all of the issues and subsequently list solutions.
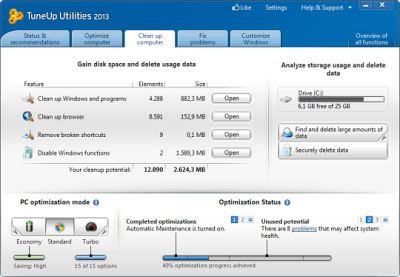
For my main machine, it was mostly registry errors and shortcuts from software testing. Clicking on the issue count will bring up a report of what TU found. From there youll have an option to choose what to ignore or fix. Looking at 500 registry errors and 345 browser items, I got the feeling that TuneUp is not very discriminating about what it labels as a problem. "Anything that can be removed in exchange for performance must go" is the philosophy here. With a click of a button TuneUp will solve all of your problems. Additionally, the utility makes backups just in case something goes horribly wrong -- good practice for whenever you stick your hands in the registry jar.

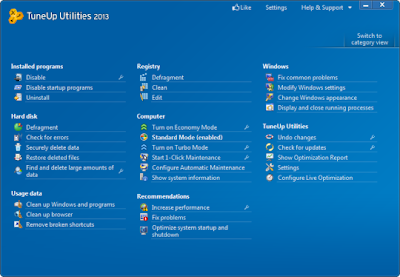
Aside from 1-Click Maintenance, TuneUp Utilities 2013 also boasts a variety of tools to speed up overall performance. TU can help with optimizing your display/animation settings, removing software, and disabling startup programs. TU also includes a new tool called "Live Optimization." Live Optimization claims to prioritize programs that run in the background and will only dedicate processing power to those applications when they are being used. I saw it running on Adobe Acrobat and IrfanView when those programs were minimized. However, the differences may not be noticeable at first. The majority of the optimizing tools require some effort on your part to customize the settings to your personal usage. Luckily, TuneUp gives you 2 extra modes: "Economy" and "Turbo" to set your optimization to your specific need.

"Economy" is nice for laptop users looking to maximize their battery life with options similar to the power-saving mode built into Windows. "Turbo" allows you to schedule optimization and cleanup frequency as to not interrupt important moments when you need to squeeze the most power out of your machine. These modes can be switched on the fly. Uninstallation was simple and tidy. TU left few traces on both my Windows 7 and Windows 8 machines after removal, although it did require me to go through Windows Control Panel to uninstall.
Overall, I felt that the utility did what it claims to do and did it well. The test PCs booted up faster with the recommended optimization, which also improved overall responsiveness when launching applications and running programs. It might not make your computer feel brand new but it should improve performance enough to hold the format monster at bay. There are some powerful optimizing tools in TuneUp Utilities that I barely scratched in this review. Intermediate users will enjoy its full functionality but novice users should still be able to get most benefits that TU offers. Take advantage of the 15-day trial and discover how TuneUp Utilities 2013 is a serious contender in the optimizing market.
Features
Start Center has a mostly blue-and-white tabbed interface that highlights five sections: Status & Recommendations, Optimize System, Clean Up Computer, Fix Problems, and Customize Windows. Each tab has several useful, clearly-defined functions that are easy for the layperson to understand. The Status & Recommendations tab, which is the apps default screen, displays the number of problems found under the Fix Problems sub-heading and the Start 1-Click Maintenance button under the Maintain System sub-head. At the bottom of the window is an Optimization Status band that fills as you complete the steps needed to whip your PC into shape. I found it a nice way to stay on top of the maintenance process.

The TuneUp Browser Cleaner quickly and easily protects your privacy by deleting traces left by Internet Explorer, Google Chrome, Opera, Safari, Firefox, and other browsers, while also optimizing browser databases. The improved TuneUp Live Optimization provides performance boosts when you need them by recalling which programs and processes slow down your PC and allowing you switch these to "Standby" mode, with the help of TuneUp Program Deactivator. In addition, TuneUp Process Manager helps you detect resource-hungry applications even faster. The easy-to-understand information on all background processes shows you exactly whats running on your PC. And last, but not least, the new cleaning features raise 1-Click-Maintenance and Automatic Maintenance to a completely new level in PC optimization.
TuneUp Utilities introduces two new tools in this years release: TuneUp Disk Cleaner and TuneUp Browser Cleaner. The former removes left over bits when programs dont cleanly uninstall; the latter removes browser activity from the likes of Internet Explorer, Chrome, Firefox, and 22 other browsers.
TuneUp Uilities 2013 is more than a basic PC clean up application. It also contains many other functions including file backup and recovery, file deletion, Windows customization, and more. Some of the features duplicate native Windows function, but its convenient to have them in one central location.
The Cleanup Process
Clicking Start 1-Click Maintenance launches the system cleaner, which scanned my test bed and displayed numerous of registry problems, broken shortcuts, and other PC problems. Clicking the "Show Details" beneath each problem count took me to a new screen that described problems in everyday language. Clicking the Start 1-Click Maintenance button cleaned up the mess, eliminating all the previously listed problems.
I returned to the home screen after that task was completed, where I noticed that the Optimization Status bar was at 50 percent. Anxious to see it hit 100 percent, I began exploring TuneUp Utilities 2013s other options that freed up disk space and repaired a handful of problems. The application identified 41 programs that potentially should be disabled. I appreciated that TuneUp Utilities 2013 displayed star ratings culled from the applications user base that helped me quickly see which software that I should keep.
Performance Improvements
After running the tests, I used the computer extensively to get a sense of how the app had changed the responsiveness of the machine. Norton Utilities delivered a noticeable performance improvement; the entire OS moved at a snappier pace even with iTunes and Photoshop open. You can download tuneup utilities 2013 here 
-300.jpg)























